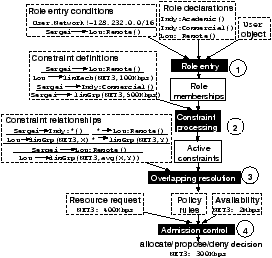
Figure 1: Policy evaluation process. A member of the Remote,Commercial roles
requests 400Kbps. The two overlapping constraints (100 Kbps, 500 Kbps) are replaced
by one granting access to the average (300 Kbps).

| Resource Management for Global Public Computing: Many Policies Are Better Than (N)one Evangelos Kotsovinos, Deutsche Telekom Laboratories; Iulia Ion, International University in Germany; Tim Harris, Microsoft Research Cambridge |
Abstract: The federation of authority in global public computing systems poses major resource management challenges, as different stakeholders may have different views on how server resources are to be apportioned. Ultimately, the complexity of declaring and managing potentially overlapping federated policies often leads to the absence of high-level resource management systems from global public computing platforms. In this paper we propose a practical system that allows the different stakeholders to independently express federated policies, provides mechanisms for resolving potential constraint overlaps automatically, and reaches decentralised resource allocation decisions. We demonstrate experimentally that the system scales gracefully, introduces only a very low performance overhead, and is suitable for operating in realistically large and complex settings.
Given a set of policy elements and a user request the process starts with the role entry step, which determines which roles a user is a member of based on role entry conditions and user properties — operation 1 in Figure 1. The next step — constraint processing — associates the roles the user shares with the constraints that apply to them. Constraints that are not associated with any of these roles are ignored further on, since they are unable to affect the admission control decision, reducing the set of constraints to the — potentially overlapping — active constraints — operation 2 in Figure 1. The overlap resolution step checks the set of active constraints against the constraint relationships, resolving overlaps and replacing them by single constraints — operation 3 in Figure 1. The algorithm starts with deriving the sets of overlapping constraints by looking for active constraints attempting to impose different reservations or limitations on access to the same resource, for each resource. Then, for each of these sets, the algorithm uses any constraint relationships that are applicable to resolve overlaps, until there are no more sets of overlapping constraints. This produces a set of non-overlapping constraints (policy rules) applicable to the request. Finally, the admission control module checks the current resource availability and usage against the policy rules to determine the maximum allowed allocation that can be made on each resource for the user in question — operation 4 in Figure 1 — and determines whether to grant or negotiate the request. In our running example, the system proposes the minimum between what the policy allows for the user, namely 300Kbps, and the available amount of resource NET3, 2Mbps. Running the constraint solver in a decentralised manner and not on a central server facilitates scalability, fault-tolerance, and inherent incentive compatibility; nodes that choose to employ sophisticated RBRM policies contribute the local server resources required to run the constraint solver. Our goal is not to pursue a “global optimum” but rather to allow server owners and other stakeholders to define how resources are to be apportioned in a decentralised, federated way.
Figure 1: Policy evaluation process. A member of the Remote,Commercial roles requests 400Kbps. The two overlapping constraints (100 Kbps, 500 Kbps) are replaced by one granting access to the average (300 Kbps).
The proposed resource management scheme needs to be lightweight enough so as to not slow down the operation of global public computing platforms considerably. It also needs to scale gracefully when policies get complex and the number of requests increases, and to be effective in expressing realistic resource management policies applied to existing systems.
This document was translated from LATEX by HEVEA.