 and
and
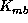 .
If we have a secure link between the customer and the merchant,
the transaction id t also can be used as a shared secret.
.
If we have a secure link between the customer and the merchant,
the transaction id t also can be used as a shared secret.
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . .
