- ... files1
- MD5 checksums
are designed to detect intentional tampering as well.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... ``difficult.''2
- A cryptographically secure
hash is defined as a hash with no known method better than brute
force for finding collisions.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... paradox''3
- The ``birthday paradox'' is best
illustrated by the question, ``How many people do you need in a room
to have a 50% or greater chance that two of them have the same
birthday?'' The answer is
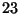 (assuming that birthdays are uniformly
distributed and neglecting leap years). This is easier to understand
if you realize that there are
(assuming that birthdays are uniformly
distributed and neglecting leap years). This is easier to understand
if you realize that there are
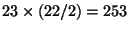 different pairs of people in the room.
different pairs of people in the room.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... system4
- LBFS uses variable sized blocks, but
has minimum block size of 2KB to avoid pathologically small block
sizes[4]
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
