 |

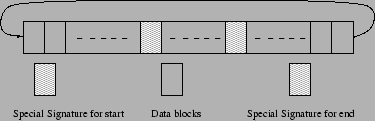
In logging, data is transient. We do not require the data of the log after the data is actually written to the data disk. To avoid problems like compaction, we use a circular log format. One design of the log is given in Figure 2. But there is a problem with the use of a special signature. Since we are writing data also, anything can be present in the data. So, there is a possibility of mistaking some data as the end signature. The next design is to have an initial signature, its offset in the log and the size of the log. We check for the signature just at that offset and if it is a valid signature, we assume that the data is completely written. However, there is still a possibility that there is some old data at that offset that exactly matches the signature. Our final design[4] reserves two entries in every block of the log disk for identification. Each block has its first few bytes as (transaction id, offset) where offset refers to the offset of the sector within the transaction. This eliminates the problem of data being mistaken as the signature since the transaction id is checked only in these places and transaction id is always unique. Hence, the structure of the transaction log has a transaction prologue, data followed by a transaction epilogue as shown in Figure 3. The space allocated to the transaction is freed only when the transaction is committed (after the data and map are written to the disk). When committing a given transaction, we change the offset value in the transaction's prologue to some special value.