|
| |||||||||||||||||||||||||||||||||||||||||||||||||||

| ||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Paper - Proceedings of the 8th USENIX Security Symposium,
August 23-36, 1999, Washington, D.C.
[Technical Program]
Antigone: A Flexible Framework for Secure Group Communication
AbstractMany emerging applications on the Internet requiring group communication have varying security requirements. Significant strides have been made in achieving strong semantics and security guarantees within group environments. However, in existing solutions, the scope of available security policies is often limited. This paper presents Antigone, a framework that provides a suite of mechanisms from which flexible application security policies may be implemented. With Antigone, developers may choose a policy that best addresses their security and performance requirements. We describe the Antigone's mechanisms, consisting of a set of micro-protocols, and show how different security policies can be implemented using those mechanisms. We also present a performance study illustrating the security/performance tradeoffs that can be made using Antigone.
|
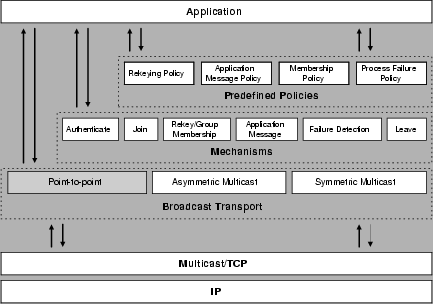 |
Described in Fig. 1, the Antigone architecture consists of three software layers; the broadcast transport layer, the mechanism layer, and the predefined policy layer.
Though not typically associated with secure communication services, the broadcast transport component provides an abstraction for unreliable group communication. A reality of today's Internet is that there are varying levels of support for multicast services. Although significant effort has been expended on the development of WAN multicasting, no single solution has been found to meet the requirements of all users. Developers specify the level of multicast support of the target environment at run time. We describe the broadcast transport layer in Section 7.
The mechanism layer provides a set of mechanisms used to implement application policies. The mechanisms represent the basic features required for a secure group. Policies are flexibly defined and implemented through the selection and interaction of mechanisms. Associated with each mechanism is a micro-protocol [HS98]. The group protocol, called a composite protocol, is defined by the composition of the mechanism micro-protocols. We identify and describe the design of the Antigone mechanisms in Section 5.
The predefined policy layer provides a suite of general purpose policies. These policies represent those commonly provided by secure group communication systems. Clearly, there are many policies beyond what is available in this layer. Where required, an application may extend or replace these policies by accessing directly the broadcast transport and mechanisms layers. We describe how the predefined polices are implemented through the Antigone mechanisms in Section 6.
![\begin{figure*}
\centerline{
\framebox[\textwidth][l]{\begin{tabular*}{6.5in}{c@...
...L,A}} $\space }
\hfill ({\it leave request}) \\
\end{tabular*}}}
\end{figure*}](img4.gif) |
We chose a composite protocol approach [HS98] for the design of Antigone mechanisms. In composite protocols, features are partitioned into modules consisting of shared state, messages, events, and micro-protocols. This approach has several desirable properties that make it applicable to Antigone. First, the modular design allows for the integration of future enhancements with minimal effect on other modules. Second, the micro-protocol approach allows state sharing between modules. We avoid the costs typically associated with state sharing between protocols (message headers).
Antigone provides mechanisms for providing the following functions; authentication, member join, session key and group membership distribution, application messaging, failure detection, and member leave. The Antigone micro-protocol variants associated with each mechanism are defined in Fig. 2. Before describing the micro-protocols, we explain the principals in the protocols and the notation used.
Fig. 3 shows the principals in an
Antigone logical group. A distinct member of the group whose identity
is known in advance to all members, called the session leader
(SL), is the arbiter of group operations such as group joins, leaves,
etc. We chose an arbitrated group because of its low cost and its
applicability to many applications. For example, in a secure
pay-per-view video broadcast application, the cable company would
provide a session leader that enforces the desired access control and
key distribution policy.
A Trusted Third Party (TTP) provides the mechanism for the session leader to authenticate joining group members. Each potential member, A, of a group (including the session leader) has a shared secret KA registered with the trusted third party (TTP). This secret key is generated and registered with the TTP before the party attempts to join any session. We assume an out of band method for registering these keys and for informing everyone about the identity of the session leader.
In our protocol descriptions, we use the term SL to refer to the
identity of the session leader, A to refer to a current or
potential member of the session, and TTP to refer to the trusted
third party. ![]() refers to message X encrypted
under the key k. The view identifier, g, is used to
uniquely tag the changing views of group membership. The term SKg refers to a session key in view g, and SKg+1 for the (next) view g+1. The term I,
possibly with a subscript, refers to a nonce value. Key distribution
protocols based on Leighton-Micali define a term
refers to message X encrypted
under the key k. The view identifier, g, is used to
uniquely tag the changing views of group membership. The term SKg refers to a session key in view g, and SKg+1 for the (next) view g+1. The term I,
possibly with a subscript, refers to a nonce value. Key distribution
protocols based on Leighton-Micali define a term ![]() ,
called a pair key, used to support secret communication between
collaborating members A and B. Derived from the pair key,
the session leader and a potential member A maintain a shared
secret key
,
called a pair key, used to support secret communication between
collaborating members A and B. Derived from the pair key,
the session leader and a potential member A maintain a shared
secret key
![]() .
A cryptographic hash for the text
x is described by H(x). We use the MD5 hash
algorithm [Riv92] in our implementation.
.
A cryptographic hash for the text
x is described by H(x). We use the MD5 hash
algorithm [Riv92] in our implementation.
The format of the identity, nonce, key, and view identifier values used in our current protocol implementation is as follows. Each identity is a unique 16 byte null terminated ASCII string of alphanumeric characters. A potential member is assigned this value when registering a long term key with the TTP. Nonce values are unique 64 bit values. To ensure that nonces are not reused, some source of monotonic values, such as the system clock, may be used. Key format is algorithm dependent. The DES standard uses an eight byte key (including eight parity bits). In the future, as other ciphers are integrated into Antigone, we will need to support other formats. The view identifier g consists of a two parts. The first part is an eight byte, null terminated name string that identifies the group, used only for displaying and debugging purposes. The second is an eight bit nonce value. Each time a new view is created (g+1), a new nonce is generated and appended to the group name string to create the new view identifier.
A policy\ block is distributed by the session leader to each group member during the authentication process. Defined by the application, the policy block is an arbitrary byte string stating the group policy. We describe the use of this data by the predefined policies layer in Section 6.
The session leader creates an asymmetric key pair (PuG, PrG) during group initialization. The public key (PuG) is delivered to potential members during the authentication process. The public key is used to reduce the cost of sending secure heartbeats from the session leader.
Where sender authenticity is configured, we assume the existence of a certificate distribution service [HFPS98]. The certificate service would provide access to certificates for each group member (CA). Note that no certificate distribution service is required in our protocol to generate or distribute the (PuG, PrG) asymmetric key pair.
We use DES [Nat77] for all encryption in the current implementation. Its inherent strength is evident from its 20-year history, yet its 56-bit key length has long been the subject of debate. Related algorithms such as triple-DES [ANS85] or DESX [KR96] offer the strength of DES with considerably longer keys. Our protocols are not tied to any specific property of DES, and may be replaced with other cryptographic algorithms as necessary.
We assume that all processes that have achieved membership, and thus have been authenticated, adhere to the system specification. We assume no member willingfully discloses its long term or session keys. All members trust the TTP not to disclose their long term key, and to generate pair keys according to the specification.
The following text describes each of the micro-protocol modules in Fig. 2. All cited message numbers refer to Fig. 2.
Authentication Mechanism - The authentication mechanism provides facilities for the authentication of potential group members. The purpose of this mechanism is twofold. First, the session leader authenticates the potential group member. Second, a shared secret between the two parties is negotiated. The shared secret, called the shared secret key, is later used to implement a secure channel between the two parties.
We use the Leighton-Micali key distribution algorithm [LM94] to authenticate the joining process and negotiate the shared secret. The main advantage of Leighton-Micali is low cost; it uses symmetric key encryption throughout, with none of the modular exponentiation operations associated with public key cryptosystems. Public key cryptography requires significantly more computation than symmetric algorithms. The de-facto standard for public-key cryptography, RSA, can be up to 100 times slower in software and 1000 times slower in hardware than DES, the predominant symmetric algorithm [Sch96].
A prospective member initiates the authentication process by sending a
message to the session leader containing her identity and a nonce
value (message 1). The session leader then obtains the pair key ![]() from the TTP (messages 2 and 3). Derived from two
identities and their associated long term keys, the pair key is used
to establish an ephemeral secure channel between the processes. To
prevent replay attacks, the session leader verifies the encrypted
nonce value I1 included in the TTP's response.
from the TTP (messages 2 and 3). Derived from two
identities and their associated long term keys, the pair key is used
to establish an ephemeral secure channel between the processes. To
prevent replay attacks, the session leader verifies the encrypted
nonce value I1 included in the TTP's response.
The session leader computes the shared secret key for communicating
with A as follows. The session leader generates the value
![]() .
This value is XOR-ed with the pair key
.
This value is XOR-ed with the pair key
![]() received from the TTP. The resulting value is a
shared secret key (
received from the TTP. The resulting value is a
shared secret key (
![]() )
that is used
to create a secure channel between the session leader and the
prospective member A.
)
that is used
to create a secure channel between the session leader and the
prospective member A.
Note that A need not communicate with the TTP to obtain
the shared secret key
![]() ;
she can
compute it directly. A decrypts the session key with this value
and validates her nonce.
;
she can
compute it directly. A decrypts the session key with this value
and validates her nonce.
After obtaining the shared secret key, the session leader responds
with an authentication response message (message 4). The response
contains the identities of the session leader and the potential group
member, and a block encrypted with the shared secret key
![]() .
The encrypted block contains the view (g) and
group member (A) identifiers, the group member nonce (I0), a
session leader nonce (I2), the policy block, and the
group public key (PuG). Upon receiving this message, the receiver
decrypts the contents and verifies the nonce I0.
.
The encrypted block contains the view (g) and
group member (A) identifiers, the group member nonce (I0), a
session leader nonce (I2), the policy block, and the
group public key (PuG). Upon receiving this message, the receiver
decrypts the contents and verifies the nonce I0.
 |
Join Mechanism - The join mechanism provides a member with facilities for gaining access to the group. The mechanism also provides measures to ensure the reliability of the join.
The potential group member (A) joins the group by transmitting message 5 to the session leader. Upon reception of message 5, the session leader validates the nonce value (I2) passed to the joining member during the authentication process. If the nonce is not valid, the join request is ignored, and the group continues. If the nonce is valid, the new member is accepted into the group. The reaction of the session leader to the join request depends on the configured group model (see below).
Note that the join message is unforgeable and fresh. A session leader knows that a correct join message is fresh and was generated by the member because of the presence of the (I2) nonce value encrypted under the shared secret key.
Mutual authentication is achieved through the verification of the secrets A and SL share with the TTP. The potential member must be in possession of the secret shared with the TTP to obtain the session leader nonce (I2) used in joining the group in message 5. The session leader must be in possession of the secret shared with the TTP to determine the secret key shared with A. A is convinced that message 4 is fresh by validating the nonce value I0 sent in the original request.
Rekey / Group Membership Mechanism - The Rekey/Group Membership mechanism provides for the distribution of group membership and session keys. We note the distinction between session rekeying and session key distribution. In session rekeying, all existing group members must receive a newly created session key. In session key distribution, the session leader transmits an existing session key.
The rekey and session key and distribution messages (6a, 6b, and 6c)
all contain a group identifier (g), the latest session leader
sequence number (SSL), and a Message Authentication Code
(MAC) calculated over the entire message, ![]() .
The group
identifier and sequence number identify the current group context.
The MAC ensures integrity of the message.
.
The group
identifier and sequence number identify the current group context.
The MAC ensures integrity of the message.
Session keys are distributed via session key blocks
(
![]() ). The intended member of each
block is identified by the group member identifier (A). The
remainder of the block is encrypted using the shared secret key
(
). The intended member of each
block is identified by the group member identifier (A). The
remainder of the block is encrypted using the shared secret key
(
![]() ). If the group identifier is decrypted by the
receiver correctly (matches the identifier in the message header), the
member is assured that the block was created by the session leader.
). If the group identifier is decrypted by the
receiver correctly (matches the identifier in the message header), the
member is assured that the block was created by the session leader.
Message 6a contains a session key block for one member, and no group
membership information. Message 6b contains a session key block for
one member and enumerates the current group membership
(
![]() ). In message 6c, a session key block is generated for
each member in the group. Group membership in message 6c is extracted
from the session key blocks.
). In message 6c, a session key block is generated for
each member in the group. Group membership in message 6c is extracted
from the session key blocks.
Rekeying is performed by the transmission of message 6c. Rekeying in Antigone is similar to key distribution after a LEAVE operation in the Iolus system [Mit97]. The session leader caches the shared secret keys, so creating this message is fast: encryption of 24 bytes (8 bytes of new session key plus 16 bytes of new group identifier) per member. Using the cached, shared secret key, the receivers of this message extract the session key out of the session key block and begin using it immediately. The size of this message grows linearly with group size, and is potentially large. In systems that provide session key independence, keying material needs to be sent to each member individually. Therefore, the size of the message is large by its nature, not as a side effect of our design. Schemes that distribute a key to each member individually will transmit the same amount of data over many more messages.
A potential problem occurs during the transition of group views. During the rekeying process, application data such as continuous media may continue to be broadcast using a previous session key. Because of delays in the delivery of the session key, a process may receive a message encrypted with a session key that it does not yet or will never possess. An application may address this issue by buffering, double encryption, dropping packets, or other approaches. We present a detailed discussion the positive and negative aspects of several of these approaches in [MHP98].
We are in the initial stages of implementing a key hierarchy based rekeying mechanism (see Section 3). It has been shown that the costs of rekeying may be vastly reduced using this approach. In the future, we will study the effect of reduced rekeying costs on policy.
Application Messaging Mechanism - The application messaging mechanism provides for the transmission of application level traffic. Each application level message is secured using cryptographic keys distributed by the rekey/group membership mechanism, or through the use of external public key certificates.
The format of application messages is dependent on the type of messaging policy. We achieve message integrity through Message Authentication Codes (MAC) [Sch96], and confidentiality by encrypting under the session key. Message 7a shows the format of a message with integrity only, message 7b shows confidentiality only, and 7c shows a message with both integrity and confidentiality.
A MAC is generated by encrypting an MD5 hash [Riv92] of the message data under the session key. A receiver confirms the MAC by decrypting and verifying the MD5 hash value. If the hash is correct, the receiver is assured that message has not been modified by some entity external to the group.
Sender authenticity (message 7d) is achieved by digital signature [DH76]. The signature is generated using the private key exponent associated with the sender's certificate. Receivers obtain the sender's certificate and verify the signature using the associated public key. Note that a byproduct of the use of digital signatures is message integrity. Our current implementation does not support sender authenticity.
Failure Detection Mechanism - An application's threat model may require the system to tolerate attacks in which an adversary prevents delivery of rekeying messages from the session leader to the entire group or to a subset of members. In such a case, some members will continue to use an old session key, a security risk if the old key is compromised. Also, for accurate membership information, it may be necessary for the session leader to be able to detect fail-stop failures of members.
In Antigone, we provide secure heartbeat messages as the mechanism to detect failed processes. The session leader detects failed processes through member heartbeats (message 8). When some number of member heartbeat messages are not received by the session leader, the member is assumed failed and expelled from the group.
Group members confirm that the session leader is still operating by receiving the session leader's secure heartbeat messages (message 9). When some number (the value of which is a policy issue for higher layers) of session leader heartbeat messages are not received, the member can assume that the session leader has failed. Heartbeat messages serve a dual purpose. In addition to failure detection, members use the heartbeats to ensure that they have the most current group state. The session leader's sequence number ensures that the heartbeat is fresh. The presence of the group identifier allows a group member to be certain that they are using the most recent session key. The heartbeats are encrypted to ensure that an adversary cannot fake heartbeats. Without these protections, an adversary may be able to prevent delivery of new session keys and trick members into continuing to transmit under an old session key indefinitely.
A member who fails to receive a current session key or membership information can attempt to recover by sending a key retransmit message (message 10). The key retransmit message indicates to the session leader that the member wishes to get the most recent group state. The session leader will send the most key/group membership distribution (message 6a, 6b, or 6c) in response to the key retransmit message. In this case, the process will be able to recover by installing the most recent session key and/or group membership.
It is worth noting that congestion that causes rekey or heartbeat message loss may be exacerbated by the resulting requests for more recent group state. This problem, known as sender implosion, is likely to limit the efficiency of Antigone in large groups or on lossy networks. We plan to introduce a retransmit mechanism similar to SRM [FJL+97] to address this limitation. Using this approach, we distribute the cost of retransmission among the group by allowing any member to respond to requests for lost messages. Retransmission requests are made a random time after the loss is detected (the random time is computed as a function of measured distance from the session leader). Members noting a retransmission request suppress local requests, and wait until a retransmission is received or a timeout occurs. Conversely, members receiving retransmission requests for data (heartbeat or key messages) they have received wait a random time (which is a function of the distance from the requester) before retransmitting. If it is noted that some other member has performed the retransmission, the request is ignored. Note that this approach in no way affects the security of Antigone, but only serves to reduce the cost of retransmission request processing.
The Antigone infrastructure's goal at this level only provides mechanisms for reliable detection of session leader's failure and not recovery from its failure. Mechanisms for detection of failures can, if desired, be used to implement recovery algorithms using primary backup or replicated approaches at higher levels.
Leave Mechanism - This mechanism provides an interface for group members to gracefully exit the group. A member sends message 11 to indicate that it is exiting the group.
The leave mechanism has a secondary purpose. Using the micro-protocol
defined in Fig. 2, a group member may request the
ejection of other members from the group. To request an ejection, the
requester places the identity of the member in the
![]() block (as B). The session leader receiving a message with this
format will eject the member in accordance with some local policy.
block (as B). The session leader receiving a message with this
format will eject the member in accordance with some local policy.
In this section, we show how flexible application policies may be implemented through the Antigone mechanisms.
Membership Awareness Policy
If members should not explicitly be given the list of current members in a group, then rekeying can be done via point-to-point messages to each member using message 6a. Otherwise, using message 6c via a multicast to rekey a group is generally more efficient. In either case, as pointed out in Section 5, we do not guarantee confidentiality of group membership against adversaries who are able to monitor network traffic and analyze packet flows in the group.
When a member fails to receive a rekey message, it can request a re-broadcast by sending message 10. If membership awareness is required in the group, the session leader can use message 6b or 6c to update the member; otherwise, the session leader can use the smaller message 6a to rekey the member, which is more efficient to encrypt and send.
Rekeying Policy Implementations
To implement a time-sensitive group, the session leader simply creates a new group identifier periodically, followed by group rekeying as describe above.
To implement a join-sensitive group, after a member joins (message 5), the session leader rekeys the session using either message 6a to each member or via message 6c.
If the policy is not join-sensitive, when a member joins, no rekeying is necessary. The new member is sent message 6b or 6a, depending on whether it needs to be provided the group membership list or not, respectively.
To implement a leave-sensitive group, when any member leaves (message 11), is ejected (message 11), or fails (detected via secure heartbeats), the session leader rekeys the group. The session leader rekeys the session by sending message 6a to each member or by multicasting message 6c to the group, depending on the membership awareness policy.
To implement a membership-sensitive group, session rekeying is done after joins, leaves, failures and ejections.
Application developers can implement other rekeying policies, given the mechanisms in the previous section. For example, the session leader can rekey only when certain members join or leave member in the group, or do time-sensitive rekeying in combination with membership-sensitive rekeying.
Application Message Policy Implementations
Several choices with different guarantees are available for sending messages (choices 7a, 7b, 7c, and 7d). It is up to the application to make judicious use of these available choices, depending on the requirements. We will discuss the performance implications of application message policies in the Performance section.
Predefined Policies
To simplify application development, Antigone provides a simple specification interface to select a group security policy. This specification interface allows selection from several common policies. Applications that require custom policies can, of course, implement their own policies directly though the Antigone mechanisms.
The predefined-policy layer in Fig. 1 uses the policy block in message 4 (see Fig 2) to send six fields (GG, SG, RK, HB, MM, and FP) to select a policy from a range of common policies.
The GG parameter is used to select from four implemented policies. The policies (TIME_SENS, LEAVE_SENS, JOIN_SENS, and MEMBER_SENS) correspond to the definitions presented in Section 2. Table 1 describes these policies in terms of their sensitivity to membership events.
The RK parameter is used to specify the rekey timer value. Each member resets the timer to the specified value when a new key is received. If the timer expires, the member considers the current session key to have expired and requests that the session leader send a new session key. The session leader should normally rekey a session prior to the expiration of this timer. Note that the combination of GG and RK parameters allow specification of rekeying policies that are both membership-sensitive as well as time-sensitive.
The SG parameter is used to specify the security guarantee on application messages. The guarantees that can be specified are: confidentiality, integrity, and sender authenticity. A side effect of the selection of any of these guarantees is that all application messages will have the group authenticity property. The group authenticity property states that messages can be verified to determine if they emanated from a member of the group. We outline the performance issues relating to these policies in Section 8.
The MM parameter is used to indicate if membership awareness is required by group members. If membership information is to be supported, it is distributed during every rekeying operation via message 6c or, in case of retransmit requests, via message 6b. Otherwise, message 6a is used to rekey members.
The failure policy (FP parameter) indicates whether failures of the session leader and the members are to be detected. If the process failure policy states failures are to be detected, heartbeat messages (9,10) are transmitted periodically. The failure detection mechanism will detect failed members as defined in the previous section.
The HB parameter is used to specify the periodicity of heartbeat messages, if any.
In general, if an adversary can prevent messages from being delivered, periodic heartbeats from the session leader are important. Since the session leader's heartbeats carry the group identifier and a sequence number, they help ensure that a group can be forced to use an old session key only for a period implied by the heartbeat interval.
Heartbeats are useful even when a combination of membership-sensitive and time-sensitive rekeying is used. For large groups, rekeying (message 6c) can be more expensive for the session leader compared to sending secure heartbeats (message 9). In such cases, the session leader can set the heartbeat interval to be lower than the rekey interval. The lower heartbeat interval ensures that members do not use an old key beyond that interval. In the absence of heartbeats, the rekey interval will define the bound for which an old key may be used.
Antigone provides three broadcast transport modes; symmetric multicast, point-to-point, and asymmetric multicast. In providing a single transport abstraction, Antigone supports network environments with varying levels of support for multicast.
The symmetric multicast mode uses multicast to deliver all messages. Applications using this mode assume complete, bi-directional communication is available via multicast. In effect, there is no logical difference between this mode and direct multicast.
The point-to-point mode provides a broadcast service based solely on point-to-point communication. All message traffic intended for the group is unicast to the session leader, and relayed to each group member via UDP/IP. However, as each message must be transmitted to group members individually, bandwidth costs increase linearly with group size. In some applications, these costs may be prohibitive. For example, a group of even modest sizes would have difficultly in maintaining a video transmission with reasonable frame rates.
In [AAC+99], we describe our experiences with the deployment of a video application based on an early version of Antigone. The deployed system was to securely transmit video and audio of the September 1998 Internet 2 Member Meeting. The receivers (group members) were distributed at several institutions across the United States. While some of the receivers were able to gain access to the video stream, others were not. It was determined that the network could deliver multicast packets towards the receivers (group members), but multicast traffic in the reverse direction was not consistently available (towards the session leader). The problem was attributed to limitation in reverse routing of multicast packets. We present significant technical detail of this issue in [AAC+99].
These problems coupled with the costs associated with a completely point-to-point solution lead us to introduce asymmetric multicast. This mode allows for messages emanating from the session leader to be multicast, and member messages to be delivered point-to-point. Members wishing to transmit a message to the group send the message to the session leader as a unicast. The session leader acts as a relay for all group communication. Any message intended for the group received by the session leader is re-transmitted via multicast. Thus, we reduce the costs associated with group delivery of a point-to-point solution to a unicast followed by a multicast.
Significant technical and administrative issues must be resolved before multicast services can be widely deployed in the Internet. In the interim, techniques such as asymmetric multicasting will be useful in the construction of group based systems.
The key advantage of a single abstraction is in its ability to handle updates in the networking environment. As symmetric multicast becomes universally available, neither Antigone nor applications built on it will require redesign to make use of the newly available service.
In this section we present a preliminary performance study of the Antigone framework. We illustrate the CPU costs of group key operations at the session leader and identify the throughput and latency characteristics of application messaging.
The experiments described in this section were performed on unloaded Intel 200MHz Pentium Pro workstations running FreeBSD kernel version 3.0. All tests were executed on an unloaded 100 MBit Ethernet LAN. Throughput and latency experiments included a single sender (which was the session leader) and nine receivers.

|
Fig. 4 shows the cost of group membership/session key message generation under varying group models and sizes. For comparison, we estimate the message generation costs associated with a key hierarchy approach.
Generation of the session key distribution message without group membership information (message 6a) should be constant under all group sizes. Creation of this message includes the generation of one session key distribution block and the generation of a Message Authentication Code (MAC). The figure indicates a constant cost of message generation.
The costs associated with key distribution with group membership message (6b) generation increases slightly with group size. This trend can be attributed to the increasing amount of data to be hashed. As the group membership grows, the costs associated with MAC generation increase.
The costs associated with the rekey message (6c) increases linearly with group size. A session key block is generated for each member, which requires a distinct cryptographic operation. Similar to the message 6b, the cost of MAC generation increases with group size. Because of the speed of the underlying cryptographic algorithms, increases in the cost of message generation due to MAC construction is significantly less than increases due to session key block construction.
The Key Hierarchy data in Figure 4 estimates the cost of rekey message with membership (similar to 6c) generation in a key hierarchy based group. In a key hierarchy, rekeying is performed by the distribution a number of keys which is roughly proportional to the log of the group size. Therefore, we see little increase in message cost as the group becomes larger. This realization further indicates that a key hierarchy based rekeying mechanism will be a valuable extension to Antigone.
|
In Table 2, we show the throughput and latency characteristics of application messaging under varying security policies. Although not surprising, our experiments show that as the number of guarantees increase, so do the costs. Thus, policy has a direct affect on performance: stronger policies have less throughput and greater latency. There is a natural ordering to these guarantees. INTEGRITY (message 7a) is least expensive, CONFIDENTIALITY (7b) is more expensive, and the INTEGRITY and CONFIDENTIALITY (7c) is the most expensive.2
The ordering of application message generation costs mirrors the speed
of the underlying cryptographic operations. We use DES
[Nat77] to achieve confidentiality, and MD5 [Riv92]
to achieve integrity. Our implementation uses the SSLeay v0.9.0b
[HY98] crypto library. On the test machine, we found
that DES encryption (
![]() Mbyte/second) is about 1/6 the
speed of MD5 hashing (
Mbyte/second) is about 1/6 the
speed of MD5 hashing (
![]() Mbyte/second).
Mbyte/second).
In this paper, we presented the Antigone framework. Antigone provides a flexible interface for the definition and implementation of a wide range of secure group policies. Applications implement policy by composing and configuring secure group primitives called mechanisms. Thus, Antigone does not dictate the available policies, but provides facilities for building them.
The mechanisms provided by Antigone represent the set of features required to implement a secure group. The mechanisms include facilities for authentication, member joins, session key and group membership distribution, application messaging, failure detection, and member leaves. Policy-implementing software use these mechanisms to construct a feature set specific to the application context and the assumed threat model.
The target applications of Antigone require a low-cost solution. A result of this requirement is that the mechanisms in Antigone provide simple, but substantive, features for implementing various security policies.
To validate the primitives as well as to simplify development of applications, we have constructed a suite of general-purpose security policies. These predefined policies represent those that have been found useful or have been suggested as being useful by various group communication systems.
Though not typically associated with secure group communication services, Antigone provides an abstract interface for multicasting. A reality of the existing Internet fabric is its inconsistent support for multicast services. In deploying multicast-based solutions, we have found that though multicast connectivity in one direction is often possible, achieving bi-directional multicast is more difficult. As a result, we introduce a transport mode called asymmetric multicasting. In asymmetric multicasting, messages emanating from a single source use multicast, and all others use unicast. Antigone's implementation provides interfaces for symmetric multicast (bi-directional), asymmetric multicast, and point-to-point (unicast) group communication.
Our initial performance study indicates that as policy requirements increase, so do the performance costs. This is not a surprising result, but indicates the need for security infrastructures to support a range of security policies. In the near future, we will extend this study to include a more thorough analysis of latency, throughput, and scalability characteristics of Antigone groups within several networking environments.
An early version of Antigone has been integrated into the the vic Videoconferencing application [Net96]. A number of policy issues arose during the implementation and deployment of the resulting Secure Distributed Virtual Conferencing (SDVC) system [AAC+99]. The current design of Antigone represents the many refinements prompted by the analysis of SDVC.
Several challenges remain. Applications may have requirements for greater fault tolerance. The need for services that provide greater scalability is evident. In the future, we hope to investigate ways to meet such requirements, while retaining simple mechanisms that support flexible security requirements.
Source and documentation for the Antigone system are available from https://antigone.citi.umich.edu/.
We would like to thank William A. (Andy) Adamson, Charles J. Antonelli, and Kevin Coffman for their assistance in the development of the Antigone system, Weston A. (Andy) Adamson for his help in constructing and maintaining the Antigone web-site, and the anonymous reviewers for their many helpful comments.
|
This paper was originally published in the
Proceedings of the 8th USENIX Security Symposium,
August 23-36, 1999, Washington, D.C., USA
Last changed: 26 Feb 2002 ml |
|