Escalating demand for digital services has motivated the community to revisit the old ideas of peer-assisted models for resource trading. Cryptocurrencies have strengthened this trend by providing a fully distributed mechanism to compensate service provision. To promote practical deployment, I present a generic framework for building decentralized service markets by utilizing these new technologies. I also discuss the security and efficiency challenges associated with the open-access work model of these markets along with some potential solutions.
When obtaining digital services, we usually deal with traditional systems that are centrally managed. Most of the time, we resort to third party providers, or commercial companies, to obtain services like file storage, content distribution, computation outsourcing, and many others. Despite being effective and widely deployed, this centrally-managed paradigm introduces several trust, cost, and transparency issues. Companies may impose complex business relationships in which customers usually overprovision their needs in order to handle future peak demands. These companies also constrain customers with the service specifications that can be offered, such as geographic coverage and speed. Not to mention infrastructure dependencies where a system implementation is tied to the API provided by the underlying resource vendors.
These issues raised many questions regarding the future of the Internet and its digital services; can we build flexible and equitable systems that allow anyone, from anywhere, to obtain or provide a service? Can we even deploy them in the form of decentralized resource markets in which computing services are exchanged for payments without intermediaries? And can we optimize these systems to be highly performant, and hence practical, without compromising security?
The pursuit of answering these questions motivated the community to revisit the old ideas of peer-to-peer (P2P) based models in which anyone is allowed to join the system and serve others. In order to encourage collaborative work and compliance with the protocol, payments are provided in return, which creates a market for trading resources. This paradigm builds flexible systems, scales more easily with demand, and extends the network coverage since peers from anywhere can join. Furthermore, P2P-based models implement transparent and equitable ecosystems in which participants can negotiate service terms and price directly instead of having a few entities monopolizing the market.However, most of existing solutions for monetizing P2P-based services introduce some form of centralization or trust. They either use centralized payment services, place trust in specific parties to handle these payments and resolve disputes, or even rely on some centralized entities to manage participants and hold them accountable. Such design choices bring us back to the central management model and the trust issues of traditional solutions.
The evolution of cryptocurrencies and blockchain technology has provided new templates for reshaping this service paradigm. Cryptocurrencies implement a decentralized virtual currency exchange medium that permits participants to be rewarded without any pre-authentication or identification requirements. And their underlying blockchains and consensus protocols support public verifiability, auditing, and decentralized governance without needing to place trust in any entity. These features can be exploited in P2P-based schemes to manage and pay for the correct service without driving the system toward centralization. Table 1 provides examples of traditional service solutions and their P2P/cryptocurrency-based counterparts.
| Service Type | Traditional Solution | P2P-based Solution |
|---|---|---|
| Payments | Banks | Bitcoin |
| File Storage | Dropbox | Filecoin |
| Video Transcoding | Amazon Elastic Transcoder | Livepeer |
| Key Management | Azure Key Vault | NuCypher |
Table 1: Examples of centrally-managed digital services and their counterparts of P2P-based ones.
Decentralized Resource Markets Design
The open access environment of P2P networks, allowing anyone to join and dealing with untrusted participants, introduces several security and performance challenges that need to be addressed before having any practical deployment. In addition, having monetary motivates attackers to attack the system in novel ways to maximize their financial profits. Thus, traditional practices of secure systems design need to be modified and expanded to account for such factors.
To address these issues, I present a generic framework for designing secure, scalable, and equitable resource markets to provide services in a fully distributed way. The proposed framework consists of systematized design steps distilled from experiences in building blockchain-based services and large-scale distributed systems. A high level diagram is captured in Figure 1. The framework accounts for the security, performance, and economic aspects of monetary-incentivized decentralized systems. The framework also highlights how such an emerging work model requires more sophisticated techniques for risk management, threat mitigation, service-payment exchange, service pricing, etc., than these employed by traditional, infrastructure-based services. These challenges, along with some potential solutions, and the framework steps are discussed in the following sections.
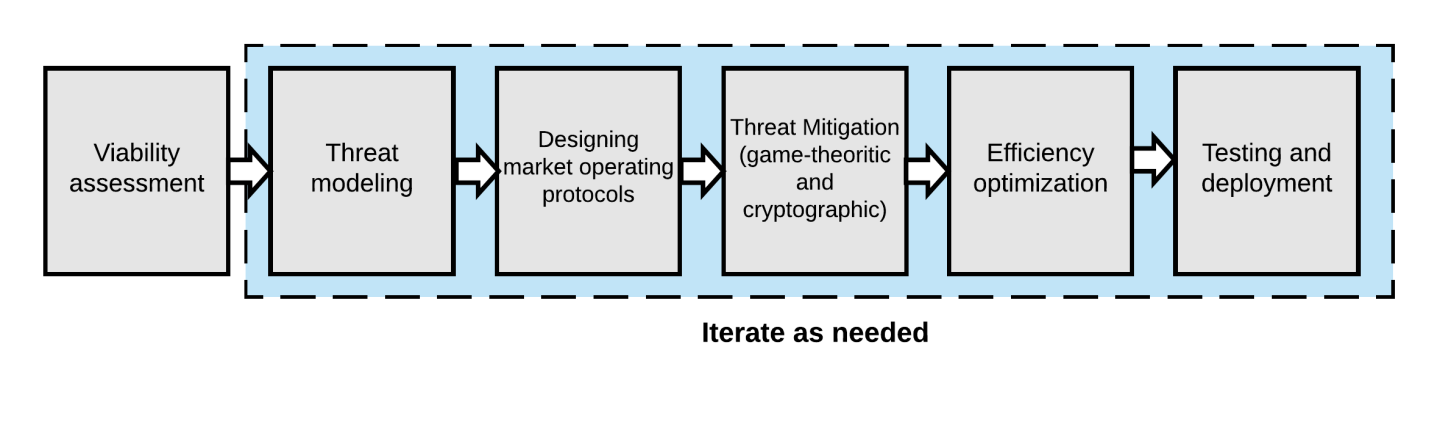
Viability Assessment Before looking into building a distributed resource market, one has to assess its viability. This includes studying the demand side (who is interested in the service) and the supply side (who can provide it) to answer several questions. Are there tangible advantages to encourage replacing traditional solutions with fully distributed ones? Can the system match the reliability and performance offered by these traditional solutions? Does providing the service require large amounts of resources that exceed the capabilities of average end-users? Such a viability assessment is an essential step to assess the potential for practical adoption before investing time and effort into building the system.
For example, in online content distribution, studies argued that up to ∼88% of the traffic can be offloaded to peers during peak demand hours [6], and several large commercial companies have utilized this option to supplement their infrastructure, such as Akamai NetSession, Swarmify, and Velocix. For file storage, a Harvard-led study [11] found that almost 50% of all hyperlinks cited in US Supreme Court opinions are broken since the content is no longer available at the cited locations. This advocates for building a decentralized content-addressed (instead of location-addressed) file storage network to promote the robustness and resilient of the web [1].
Threat Modeling Despite the many advantages they offer— decentralization, transparency, and lowered service costs— there is still a big gap between the promise of P2P-based systems and their performance in practice. Adding monetary incentives, by using another P2P-based payment service, i.e., cryptocurrencies, widens this gap. This is due to the perception that these systems are not secure, where the recent large number of security breaches give credence to these doubts [2].
The best practice for designing a secure system requires a threat modeling step to investigate potential security risks. Such a model can guide designers in deploying the proper countermeasures, and evaluating the security level of the system in the after design stage. For resource markets, building a threat model requires a framework that can handle large-scale distributed systems, explicitly account for the financial motivations of the attackers, and help in spotting any potential collusion between these attackers.
Thus, existing threat modeling frameworks, which either target secure software development or small-scale systems, need to be adapted to address these issues. For example, the ABC framework [3] was designed to achieve these goals by accounting for both the underlying cryptocurrency medium and the service provided on top of it. ABC enables building comprehensive threat models by holistically analyzing the threat space while managing its complexity, and distilling the impactful cases that need to be neutralized. ABC also allows for classifying threats based on their mitigation techniques, that is, threats that can be addressed cryptographically or algorithmically, and those that require game theoretic means, thus providing insights about the proper measures to deploy.
It should be noted that the threat modeling step needs to be revisited each time the system design is altered. Furthermore, it should be performed as the last step before shipping the system to argue formally about its security.
Unique Aspects of Operating a Decentralized Market Operating in a flexible open access ecosystem comes at a cost. Dealing with untrusted parties means that fair exchange is impossible [8], which raises the question of when to pay servers — before or after providing the service? If paid first, a malicious server may not serve the customer, and if served first, a malicious customer may not pay afterwards.
Moreover, accounting attacks, in which participants collude with each other, pretending that the service has been delivered, could be a hammer that destroys the market. This is a particular problem in systems that require sponsoring service requests. For example, in content distribution, a publisher (for example, Netflix) can hire caches (or servers) to distribute content to its clients, and hence, it pays for the service. In this case, caches (or servers in general) and clients may collude so that clients pretend to be served, allowing servers to collect payments from the publisher (the sponsor) for free.
These security issues (and many others depending on the service type) require a careful design of a decentralized service-payment exchange protocol that can reduce the risks of dealing with untrusted, possibly colluding parties. Such a protocol represents the backbone of the resource market; if it fails the whole market fails. Servers will not be willing to participate if they are not being paid. The same holds true for customers; they will not be willing to use the system if they pay for a service that they do not receive. Operating the market also requires devising mechanisms for service pricing, term negotiation for server recruiting, and matching protocols to match these servers with interested customers.
Financial and Cryptographic Security Measures Usually, security threats are mitigated by using cryptographic means (encryption and digital signatures), algorithmic approaches (ordering the actions in a way that enforces secure behavior), or a variety of network/systems security techniques (firewalls and access control mechanisms). Monetary-incentivized systems introduce new types of attacks that cannot be addressed using conventional approaches. In particular, having financially-motivated attackers may require addressing certain threats using financial techniques. These fall into three categories. Detect-and-punish mechanisms, where parties are required to lock penalty deposits that are forfeited if they are caught cheating. Designing algorithms that, if performed maliciously, require larger amounts of resources than when performed honestly. Or devising service pricing and payments mechanisms that make it more profitable on the long run to act honestly in every service request than cheating or ignoring the request (even if cheating or ignoring are not detectable). Such techniques make cheating unprofitable so that rational parties will choose to adhere to the protocol.
For example, to reduce the risks of the impossibility of fair exchange, micropayments can be employed. That is, instead of paying a large chunk of money for the full service, the payment is divided into small values, each of which is exchanged for a small service amount. For instance, one can pay for retrieving a file in small data chunks instead of paying for the full retrieval all at once. Hence, a server loses a small payment if a client does not pay after receiving a chunk. Similarly, a client loses a small payment if it pays in advance and the server does not send a data chunk in return.
Optimize for Efficiency Although designing a secure system is the ultimate goal, efficiency is an important driving factor of practical adoption and deployment. System designers need to exploit any opportunity that allows for optimizing performance. This also involves choosing the right trade-off between security and efficiency in the sense of risk management. That is to say, threats that have high impact need to be prioritized over low impact ones. In addition, looking into alternative cryptographic primitives that are lightweight (or optimizing their implementation) while maintaining the required security guarantees is another effective venue to utilize.
Another important aspect is system scalability— whether it is in terms of interactivity, amount of data exchanged between the participant, or the amount of data logged on the blockchain. A prime example is employing (distributed) probabilistic micropyament schemes [10], [7], [4] to aggregate small transactions into few larger ones before processing. In such scheme, payments take the form of lottery tickets, and only winning tickets are processed in the system with values that compensate properly for the tickets exchanged so far. Another example is batching client requests and replies together to reduce interaction, or even batching work confirmations to reduce the amount of data logged on the blockchain.
Testing and Deployment To examine the viability of the system, conventional practices of prototyping, benchmarking, and controlled deployment can be used to evaluate both efficiency and resistance to attacks. These provide a starting point to attract early adopters and test the system at a large scale. Nowadays, it is popular in blockchain-based systems to have what is called a testnet, that runs with fake coins, to serve this purpose. This testing stage may inspire designers to revisit specific parts of the system for further optimization based on the results of the conducted experiments, or feedback from the community even after the official launch (or production stage).
Conclusion
Decentralized resource markets represent a monetized version of P2P-based systems that evolved to build flexible, equitable, and transparent ecosystems. In order to encourage practical deployment, in this article I put forward a generic framework for designing efficient and secure resource markets. The framework is distilled from experiences in building blockchain-based large-scale systems. In particular, cryptocurrencies and their blockchains have drawn a huge interest recently as a powerful economic tool. This resulted in a rush into implementing novel ideas without a thorough design process, leaving the produced systems vulnerable to sever security risks. The presented framework is believed to provide a useful guiding maps to avoid such pitfalls.
Reference
[1] Filecoin
[2] The Largest Cryptocurrency Hacks So Far
[3] Almashaqbeh, G., Bishop, A., and Cappos, J. Abc: A threat modeling framework for cryptocurrencies. In IEEE INFOCOM Workshops - CryBlock (2019).
[4] Almashaqbeh, G., Bishop, A., and Cappos, J. Microcash: Practical concurrent processing of micropayments. In Financial Cryptography and Data Security (2020).
[5] Almashaqbeh, G., Kelley, K., Bishop, A., Cappos, J. Capnet: A defense against cache accounting attacks on content distribution networks. In IEEE CNS (2019), IEEE, pp. 250–258.
[6] Anjum, N., Karamshuk, D., Shikh-Bahaei, M., Sastry, N. Survey on peer-assisted content delivery networks. Computer Networks 116 (2017), 79–95.
[7] Chiesa, A., Green, M., Liu, J., Miao, P., Miers, I., Mishra, P. Decentralized anonymous micropayments. In Eurocrypt (2017), Springer, pp. 609–642.
[8] Even, S., Yacobi, Y. Relations among public key signature systems. Technical report, Computer Science Department, Technion, 1980.
[9] Fisch, B. Tight proofs of space and replication. In Annual International Conference on the Theory and Applications of Cryptographic Techniques (2019), Springer, pp. 324–348.
[10] Pass, R., Shelat, A. Micropayments for decentralized currencies. In CCS (2015), ACM, pp. 207–218.
[11] Zittrain, J., Albert, K., and Lessig, L. Perma: Scoping and addressing the problem of link and reference rot in legal citations. LIM 14 (2014), 88.

