- ... Center1
- This work was done at the
HP Systems Research Center in Palo Alto. The authors with differing
current affiliations are: Andersen, MIT; Burrows and Thekkath,
Microsoft Research; Mann, VMware.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... blocks2
-
For simplicity, this example assumes that the file's blocks can be
described using only one capability; in practice, highly fragmented
files may require multiple capabilities because capabilities have a
fixed size so that they can fit in a packet.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ...3
-
The reader might be wondering whether the application of a MAC to
its own output has somehow compromised its cryptographic
properties.
This is not the case, and the intuitive argument is as
follows: Suppose that it was feasible for
an adversary who does not know the value of
 to produce values
to produce values 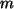 ,
,
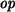 , and
, and  such that
such that
 . Then by the
unforgeability property of
. Then by the
unforgeability property of  mentioned above, the adversary must
know the value of
mentioned above, the adversary must
know the value of 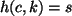 . Thus, the adversary can produce
. Thus, the adversary can produce
 and
and  such that
such that 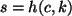 . Therefore, by applying the
unforgeability property again, the adversary must know the secret key
. Therefore, by applying the
unforgeability property again, the adversary must know the secret key  ,
a contradiction.
,
a contradiction.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... ID.4
- Note that the group ID's cannot be recycled, which means that in theory the system will
eventually run out of space. But by using relatively few bits for the
group ID's--say 64 bits--it will take longer than the life of the
system for that to happen.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... NFS.5
- A higher
level of consistency could be implemented using the same basic
technique as Spritely NFS [24]: channeling reads
and writes for non-exclusive-mode files through the metadata server.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
- ... protocol.6
- We would
store blocks encrypted on disk, but the keys would be managed by the
metadata servers.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
.
