
Next: Data Layout
Up: Design of TSS
Previous: Pseudo Device Driver Approach
Figure 1 shows the overview of the TSS device.
The TSS device can be divided into a lower level pseudo device driver and
a set of user level routines. The pseudo device driver consists of:
- RAID1, RAID5 and cRAID5 -
The driver code that handles the requests to corresponding RAID devices.
- Integrated Device -
The driver code that provides a unified view of the
multiple RAID device types under it. It also takes care of victimization (RAID1 to RAID5 for example) and
promotion (RAID5 to RAID1 for example) of stripes.
- Data logging -
Data logging is used to keep data consistent across crashes. This is done by
using an additional partition for logging, synchronously logging each
request before doing any writes to the data disks, and synchronously
committing the log entry after the write is complete in all the data disks.
- Metadata Persistence -
For the data to be consistent in the TSS device, the metadata about the
logical stripes, their
mapping to the physical stripes, information about the compressed stripes etc,
needs to be persistent across reboots. This is taken care of by using a
separate private partition, which is used to hold the metadata of the TSS
device.
- Performance Measurement Driver (ganak) -
To keep track of the number of accesses and the time taken by the access of
TSS device driver, one more pseudo device driver (ganak) has been developed. This
gets requests from user level routines, maintains some counters, and in turn
does the read/write on the TSS driver.
Figure 1:
TSS High Level Design
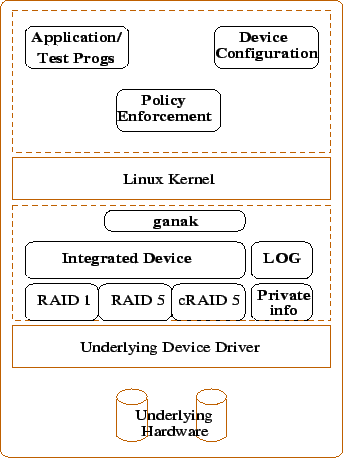 |
The user level routines for the TSS device support:
- Device Configuration -
These are a set of routines which are used to
configure the TSS device. They can be used to specify both general device
information and the personality specific information. The configuration
information is parsed using lex and ioctl() calls used to communicate the
configuration information to the TSS device driver.
- Policy Enforcement -
The management of stripes at different RAID levels
depending on the temperature is done by the Policy Enforcement routines.
These routines run as a daemon process at user level. They collect the
information about the stripes using suitable ioctl() calls, analyse the
information and take decisions for dynamic stripe management, by
suitably promoting / victimizing the stripes.
- Application/Test Programs -
Some user level routines (as application programs) are available to test the
functionality of the TSS device. These include routines to read the trace and
apply requests to the TSS device. These again use the read()/write()/ioctl() interface of the TSS device.


Next: Data Layout
Up: Design of TSS
Previous: Pseudo Device Driver Approach
2001-09-13

