



Next: Performance Estimation
Up: On the implementation of
Previous: The AddRoundKey transformation
Although there is a large variety of possible physical attacks on the AES, cf.
[AG,BS99,BS02,CJRR,DR1,KQ,KWMK,Me,YT],
the
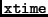 operation is clearly the most critical one in the AES algorithm,
at least with respect to physical security or so called side-channel attacks.
Namely, this operation involves a multiplication that is subject to timing and fault attacks (see [KQ, BS02]).
We also stress that the recently developed fault based susceptibility due to [BS02] cannot be avoided
by the simple dedicated fault-tolerant AES hardware as proposed by [KWMK].
However, thanks to the implementation described here, the aforesaid timing attack on the
operation is clearly the most critical one in the AES algorithm,
at least with respect to physical security or so called side-channel attacks.
Namely, this operation involves a multiplication that is subject to timing and fault attacks (see [KQ, BS02]).
We also stress that the recently developed fault based susceptibility due to [BS02] cannot be avoided
by the simple dedicated fault-tolerant AES hardware as proposed by [KWMK].
However, thanks to the implementation described here, the aforesaid timing attack on the
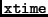 operation doesn´t work.
This is due to the fact that the timing behaviour of modern crypto coprocessors is independent of its operands,
which indeed avoids a timing attack vulnerability of our implementation.
Moreover, by performing the
operation doesn´t work.
This is due to the fact that the timing behaviour of modern crypto coprocessors is independent of its operands,
which indeed avoids a timing attack vulnerability of our implementation.
Moreover, by performing the
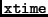 operation on 16 bytes in parallel we make fault attacks very difficult to achieve,
because we can use a fault in the calculation to flip a bit, but the flipped bit
can be any one of the 128 bits of the state or temporary variable.
Another critical part of the implementation described here might be the transfer of data through the so
called X-BUS, the bus that connects the CPU and the coprocessor.
This transfer of data is more significant when the AND and Rotate operations are not supported by the coprocessor and
therefore have to be performed within the standard CPU.
The bus contents could then be tampered via an electronic microscope, a focused ion beam,
or could be revealed through measuring the power consumption or even by an electromagnetic field analysis.
Fortunately, this X-BUS is by some
operation on 16 bytes in parallel we make fault attacks very difficult to achieve,
because we can use a fault in the calculation to flip a bit, but the flipped bit
can be any one of the 128 bits of the state or temporary variable.
Another critical part of the implementation described here might be the transfer of data through the so
called X-BUS, the bus that connects the CPU and the coprocessor.
This transfer of data is more significant when the AND and Rotate operations are not supported by the coprocessor and
therefore have to be performed within the standard CPU.
The bus contents could then be tampered via an electronic microscope, a focused ion beam,
or could be revealed through measuring the power consumption or even by an electromagnetic field analysis.
Fortunately, this X-BUS is by some 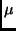 -controller ICs vendors protected by hardware and/or software mechanisms.
Among the hardware countermeasures there are active shields or random bus scrambling techniques available
on some existing high security m-controller ICs.
Last generation of those high securit
-controller ICs vendors protected by hardware and/or software mechanisms.
Among the hardware countermeasures there are active shields or random bus scrambling techniques available
on some existing high security m-controller ICs.
Last generation of those high securit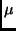 -controller ICs are designed using a special dual rail security logic,
cf. [MAK,MACMT].
This logic not only ensures that both, a ``0" and a ``1" have the same Hamming weight,
but also that changes between a logical ``0" and a logical ``1" are not distinguishable by an adversary.
As software measures some masking and encryption techniques could be applied to the data before being transferred,
both in the CPU and in the coprocessor.
However, these measures may have a significant impact on the overall performance of the algorithm,
which makes the aforesaid hardware countermeasures the practically preferred choice.
-controller ICs are designed using a special dual rail security logic,
cf. [MAK,MACMT].
This logic not only ensures that both, a ``0" and a ``1" have the same Hamming weight,
but also that changes between a logical ``0" and a logical ``1" are not distinguishable by an adversary.
As software measures some masking and encryption techniques could be applied to the data before being transferred,
both in the CPU and in the coprocessor.
However, these measures may have a significant impact on the overall performance of the algorithm,
which makes the aforesaid hardware countermeasures the practically preferred choice.



Next: Performance Estimation
Up: On the implementation of
Previous: The AddRoundKey transformation
Roger Fischlin
2002-09-25
