 |

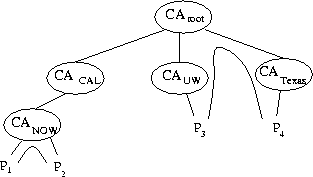
The manner in which the hierarchy is traversed is based on the theory presented in [Birrell et al. 1986]. In this model, a CA cannot speak for a principal who belongs to a descendant's domain, allowing separate administrative domains to maintain local autonomy. Thus, a principal receiving a certificate endorsed by a CA in a foreign administrative domain believes the certificate valid only if a path of trust is present from the local domain to the remote domain. The presence of such a path is determined by traversing the least common ancestor of the two domains in the CA hierarchy. Principals trust their local CA more than any of the CA's ancestors in the CA hierarchy. Thus, if an ancestor of a CA is compromised, transactions among local principals are not affected, increasing system availability and keeping trust as local as possible.
 |
Figure 3 depicts an example of the arrangement of principals in multiple administrative domains. In this example, Principals P3 and P4 must establish a path of trust through the root CA to successfully authenticate one another. Demonstrating the principle of locality of trust, Principals P1 and P2 need only establish a path of trust through their common ancestor one level up to mutually authenticate.