
We here describe a very simple example of an attack using a trojan horse Java applet. The reader with imagination will have no trouble constructing a more elaborate example that would be sensitive to the specific browser and client platform used, and could do a broader range of sophisticated attacks.
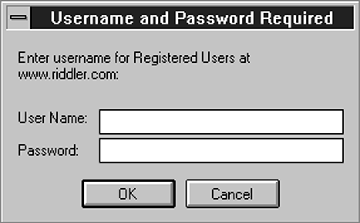
The Netscape Navigator browser uses a standardized dialogue box to request username/password pairs when a web server responds to an http request with a demand for authentication. Figure 1 shows the appearance of the authentication dialogue box used by WindowsNT Netscape. To demonstrate the use of Java for trojan horse attacks, we have written an applet which fakes the appearance and behavior of this dialogue box; for the interested reader, this applet can be found at https://blind.trust.cs.cmu.edu/spoof.html.
Figure 1: Authentication dialogue box displayed by WindowsNT Netscape browser
The applet attempts to trick users into believing that they are authenticating themselves as usual to a particular web site. This is done by mimicking the appearance and behavior of the real site within the browser window. If the user clicks on a link that would cause the real site to request authentication, the applet displays its fake authentication dialogue box; clicks on other links are handled by loading the correct pages from the real web site. If the fake dialogue box fools the user into entering their username and password, the applet sends the stolen information back to a waiting process on blind.trust.cs.cmu.edu via socket connection, tells the user that the web site server is not responding, and loads the real web page from the real web site, so that the user's next attempt will succeed.
Implementing this applet required fewer than 200 lines of
Java code![]() . As shown in
Figure 2, our applet uses a simple image of an actual authentication
dialogue box, acquired by screen capture and edited in Adobe Photoshop,
to mimic the appearance of the dialogue box within the browser window.
Actual Java TextField objects are drawn on top of the image to
provide the necessary pair of editable text fields. We overloaded
the applet event handling routines in order to make the simulated
buttons on the dialogue box behave appropriately in response to mouse
events, including performing the necessary socket communication and
http request when either button is actually pressed.
. As shown in
Figure 2, our applet uses a simple image of an actual authentication
dialogue box, acquired by screen capture and edited in Adobe Photoshop,
to mimic the appearance of the dialogue box within the browser window.
Actual Java TextField objects are drawn on top of the image to
provide the necessary pair of editable text fields. We overloaded
the applet event handling routines in order to make the simulated
buttons on the dialogue box behave appropriately in response to mouse
events, including performing the necessary socket communication and
http request when either button is actually pressed.
Figure 2: Our trojan horse version of the authentication dialogue box
This applet was created in order to demonstrate a point, and as such, it does not currently present a seamless attack. For example, the alert user may notice that the dialogue box is not draggable, or that the Location URL displayed by Netscape is not what the user expected (however, this is located in a position where many users might ignore the information displayed by Netscape). Some of the current limitations could be fixed by putting more work into the applet, while others, like the Location URL, are effectively enforced by Netscape.
This attack can easily be generalized to mimic any user interface element that has a standardized appearance and requests sensitive information from the user; some other obvious examples of such information are credit card numbers for electronic commerce applications, account numbers for banking, or, in the case of hospitals, a wide variety of potentially sensitive medical information.