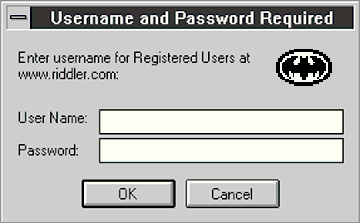

Figure 3: Authentication dialogue box protected by personalization
Trojan horse attacks such as we have described rely on imitating the visual appearance of some program that the consumer already trusts with sensitive information. Standardized user interface appearance is a great help to the designers of such attacks, since it removes the problem of determining what appearance the consumer expects.
We propose that programs which require the consumer's trust should employ window appearances which are easily recognizable to the consumer yet difficult to predict by an attacker. The obvious mechanism for accomplishing this is to require the consumer to personalize the appearance of the software at the time the trust relationship is formed, which may be installation or account initialization depending on the application involved. Figure 3 shows a hypothetical user's personalization of the Netscape dialogue box with a Batman logo. Our trojan horse attack would not be able to predict this personalization, and its ability to fake the appearance of the real dialogue box would be substantially weakened.
As another example, consider a SET dialogue box. If the dialogue box has a standardized, predictable appearance, it will be an easy target for a similar trojan horse interface-emulator applet. On the other hand, suppose that the consumer is able to select a background display for the dialogue box (out of a range of thousands of potential displays). As long as the Java applet is not able to determine what the background display expected by that particular consumer is, the applet will not be able to credibly simulate the user interface of the program under attack.
In order for this strategy to be most effective, the trusted application should not only require the consumer to participate in a personalization process, but should, within that process, strongly convey to the consumer the importance of not trusting any window that does not display characteristics in conformance with the personalization. The process should also be designed to maximize the unpredictability of the consumer's personalization choices; for example, when offering the consumer a choice of window backgrounds, it would be best to offer more than just two or three backgrounds to choose from, and to present the possible backgrounds in a randomized ordering or layout to compensate for the fact that most consumers may simply choose the first option they are given.
Window personalization is most effective against attackers who either do not have an opportunity to find out the potential victim's personalization choices, or who are not interested in creating a trojan horse designed to fool a specific individual.